Verifying Protection Status
There are several ways to verify that your application has been successfully protected with ByteHide Shield.
Verification Methods
Shield provides multiple methods to confirm that your application has been protected correctly:
- Security Certificates (Enterprise edition)
- Cloud Panel History
- Programmatic Detection using ByteHide.ToolBox
Let's explore each option in detail.
Security Certificates
Enterprise
With the Enterprise edition, you receive an official security certificate for each protected application. This certificate provides:
- Verification that the specific application has been protected
- Date and time when the protection was applied
- List of protections that were successfully applied
- Unique identifier for the protection session
This certificate serves as official documentation that your application has been protected with ByteHide Shield, which can be important for compliance and security auditing purposes.
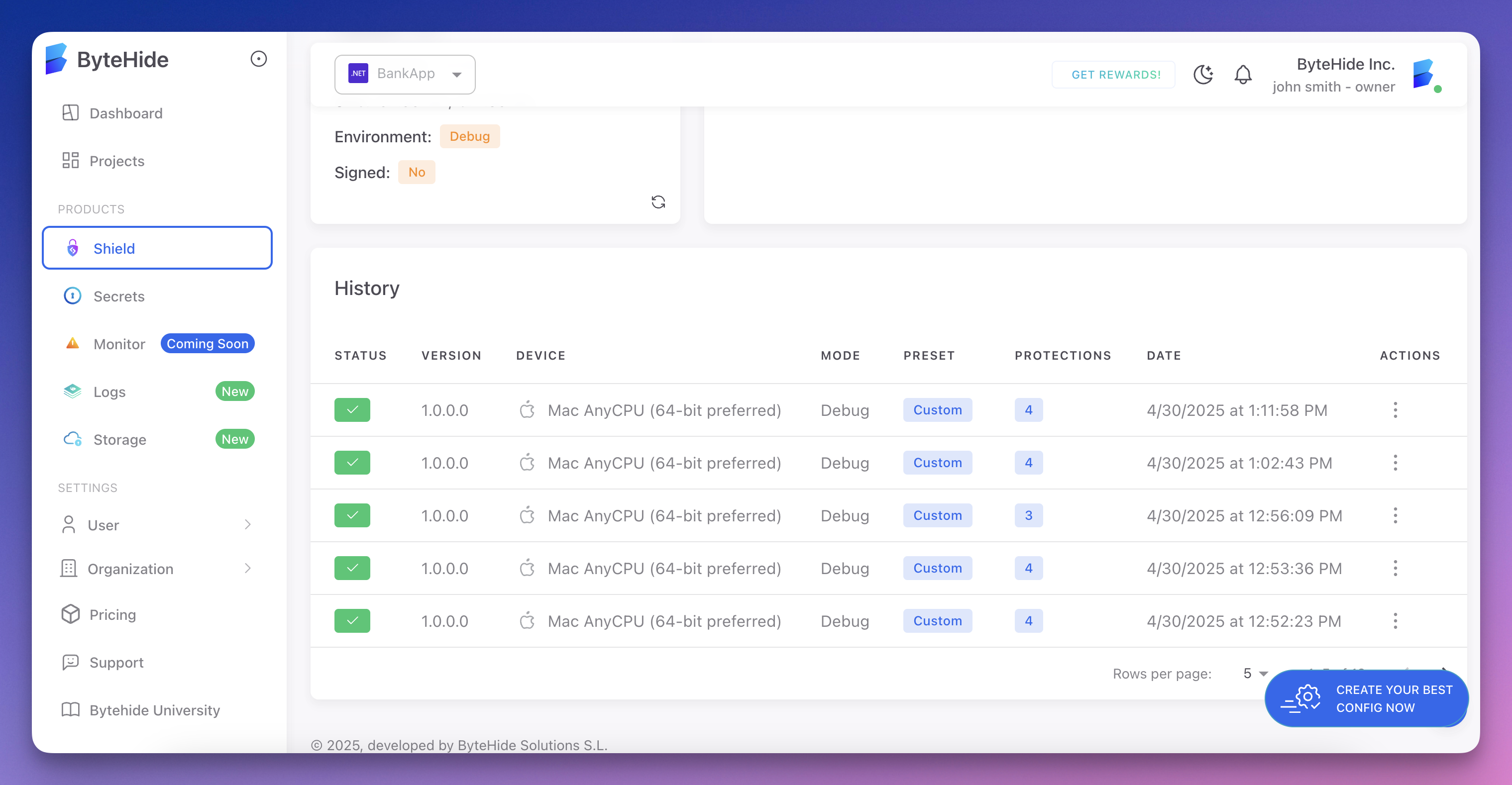
Cloud Panel History
All ByteHide Shield users can verify protection status through the ByteHide Cloud Panel. To check:
- Log in to your ByteHide account
- Navigate to the Protection History section
- View the list of all protected applications along with:
- Protection date and time
- Applied protections
- Status of the protection process
- Download links for protected assemblies
 Click to expand
Click to expand
The cloud panel provides a comprehensive history of all your protection operations, allowing you to verify that specific applications have been protected with the correct settings.
Programmatic Detection
You can also verify protection status programmatically from within your application using the ByteHide.ToolBox package.
Installation
First, add the ByteHide.ToolBox package to your project:
dotnet add package ByteHide.ToolBox
Checking Protection Status
Use the following code to detect if the current assembly is protected:
using ByteHide.ToolBox;
// Check if current assembly is protected
bool isProtected = Products.Shield.IsObfuscated();
// Display protection status
Console.WriteLine($"Application is protected: {isProtected}");
Best Practices
- Automated verification: Consider adding protection verification to your CI/CD pipeline
- Regular audits: Periodically verify that all production applications are properly protected
- Multiple methods: Use more than one verification method for critical applications
While detecting if an application is protected is useful, the specific protections applied and their configurations are intentionally difficult to determine from outside the application. This is by design, as exposing this information would reduce security.
Compatibility
The programmatic detection methods work with all .NET frameworks and project types. Whether you're verifying libraries, applications, or modules, you can confirm their protection status using the methods described above.