Security Settings
ByteHide provides comprehensive security settings to protect your log data and control access to your logging infrastructure.
Project Token Management
Your project token is the primary authentication mechanism for ByteHide Logger.
 Click to expand
Click to expand
Current Token
- Token Display: Project token shown as
bh_rD13Y...(partially masked for security) - Copy Function: "Copy this token into your project configuration file" button
- Secure Storage: Store token securely in your application configuration
Token Security
- Unique Identifier: Each project has a unique token
- Authentication: Required for all logging operations
- Rotation: Tokens can be reset when compromised
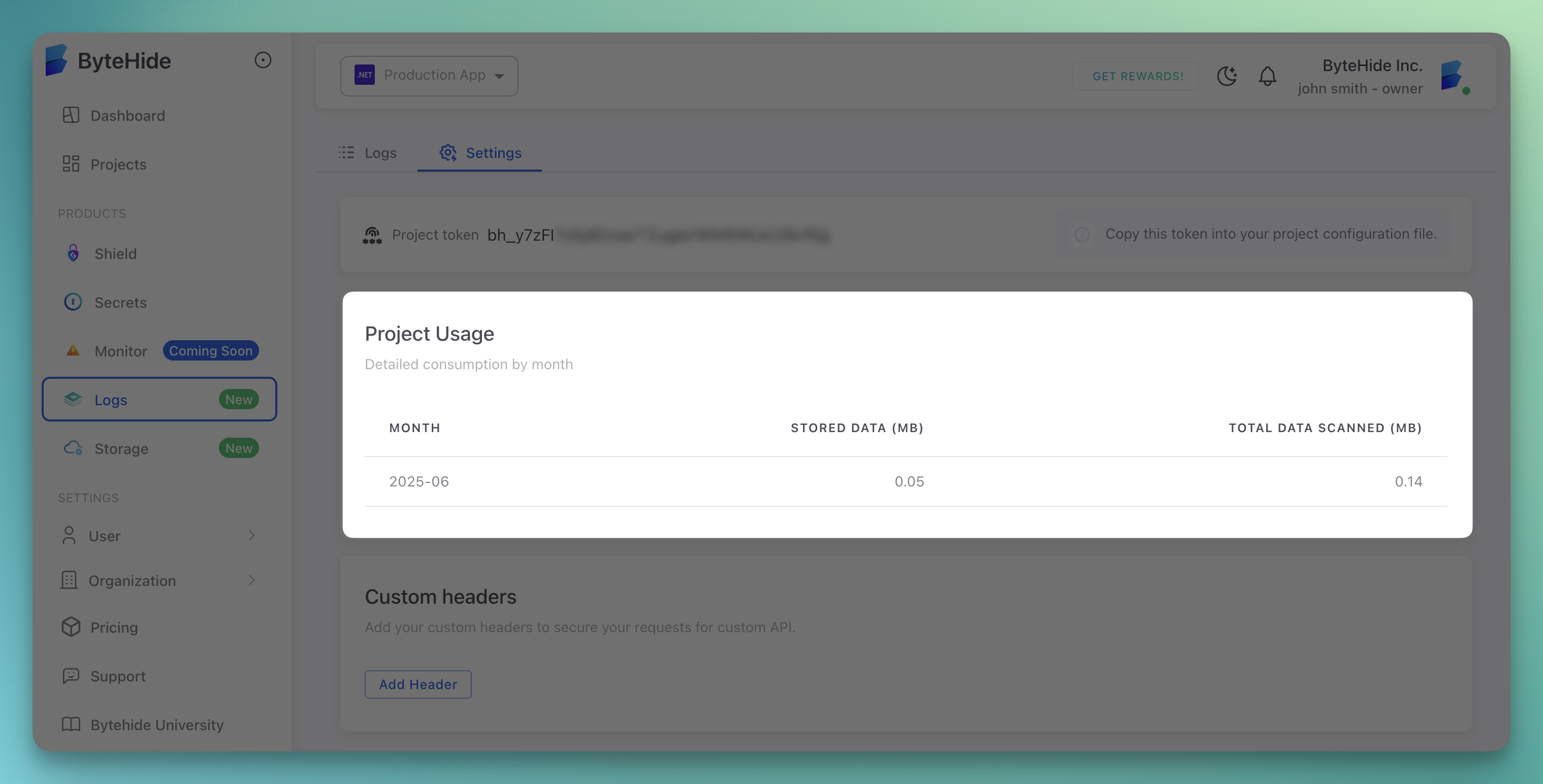
Project Usage Monitoring
Track your project's logging usage and data consumption.
 Click to expand
Click to expand
Usage Metrics
- Month: Monthly usage tracking (e.g., "2025-06")
- Stored Data (MB): Amount of log data stored (e.g., "0.38 MB")
- Total Data Scanned (MB): Total data processed (e.g., "28.54 MB")
Data Management
- Monitor storage consumption
- Track data processing volumes
- Plan capacity based on usage trends
Custom Headers
Configure custom headers for secure API requests and additional authentication.
 Click to expand
Click to expand
Header Configuration
- Add Header: Button to add new custom headers
- Security Enhancement: Add custom headers to secure your requests
- API Integration: Support for custom API authentication
Use Cases
- Additional Authentication: Layer extra security on API calls
- Request Identification: Add unique identifiers to requests
- Compliance: Meet specific security compliance requirements
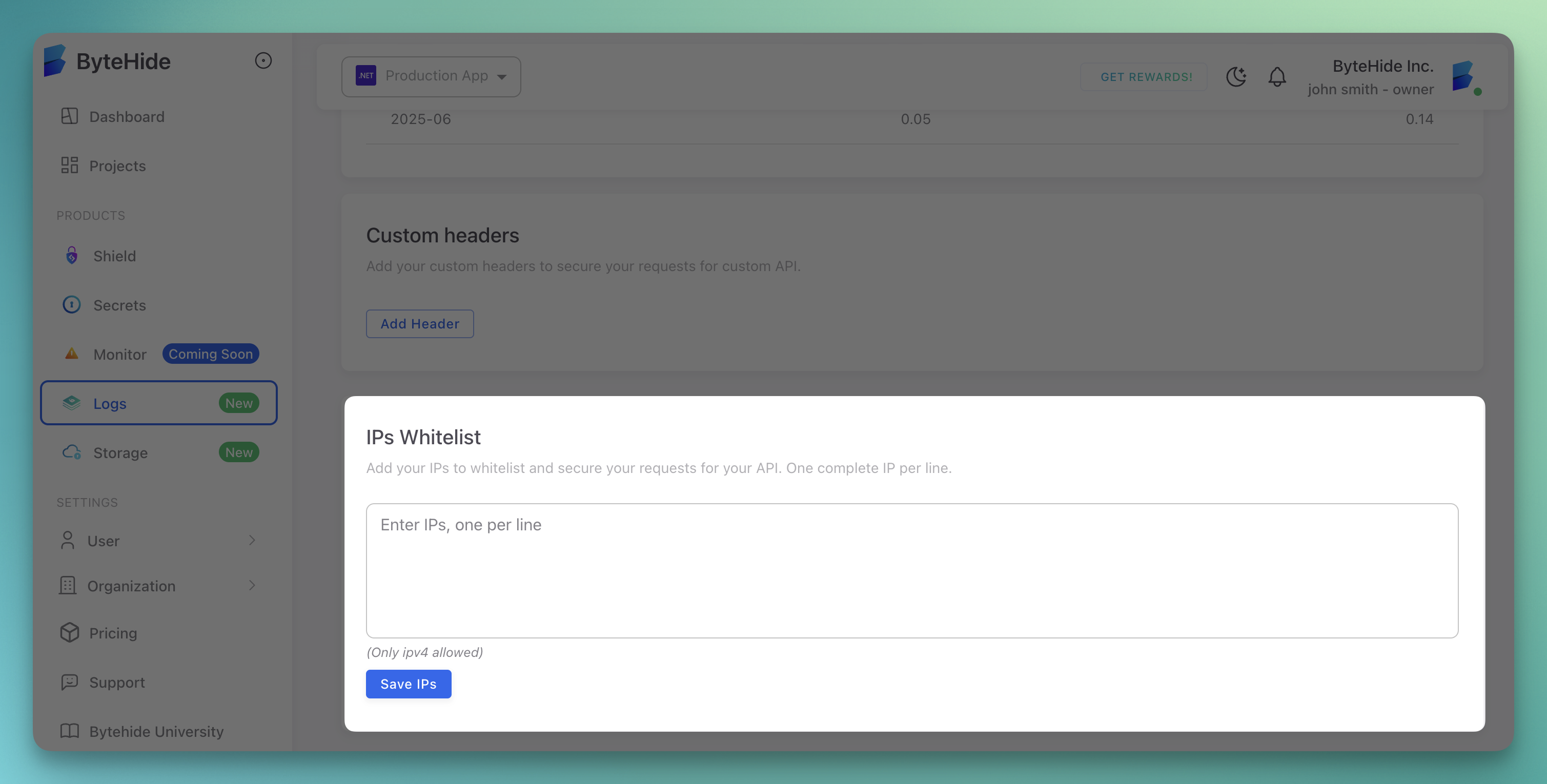
IP Whitelist
Control access to your logging infrastructure by restricting allowed IP addresses.
 Click to expand
Click to expand
Whitelist Configuration
- IP Entry: Text area for entering allowed IP addresses
- One Per Line: Enter one complete IP address per line
- IPv4 Support: Currently supports IPv4 addresses only
- Save IPs: Button to apply whitelist changes
Security Benefits
- Access Control: Limit which networks can send logs
- Threat Reduction: Prevent unauthorized log submissions
- Compliance: Meet network security requirements
Example Configuration
CODE
192.168.1.100
10.0.0.50
203.0.113.25192.168.1.100
10.0.0.50
203.0.113.25Token Reset
Reset your project token when security is compromised or for routine security maintenance.
 Click to expand
Click to expand
Reset Process
- Reset Button: Red "Reset project Token" button
- Immediate Effect: Token reset takes effect immediately
- Update Required: Update all applications with new token after reset
When to Reset
- Security Breach: When token may be compromised
- Team Changes: When team members leave
- Routine Security: As part of regular security practices
- Compliance: To meet security audit requirements
Security Best Practices
Token Management
- Secure Storage: Store tokens in secure configuration systems
- Environment Variables: Use environment variables, not hard-coded values
- Regular Rotation: Rotate tokens periodically
- Access Limitation: Limit who has access to tokens
Network Security
- IP Restrictions: Use IP whitelist for production environments
- VPN Access: Consider VPN requirements for log access
- Network Monitoring: Monitor for unusual network activity
Access Control
- Team Permissions: Control who can access security settings
- Audit Logging: Track changes to security configurations
- Regular Reviews: Periodically review access permissions
Configuration Steps
Initial Setup
- Copy Token: Copy project token from settings
- Configure Application: Add token to your .NET application
- Test Connection: Verify logging works correctly
- Set IP Whitelist: Add your application server IPs
Security Hardening
- Enable IP Whitelist: Restrict access to known IPs
- Add Custom Headers: Implement additional authentication
- Monitor Usage: Regularly check usage metrics
- Schedule Token Rotation: Plan regular token updates
Compliance Features
Data Protection
- Encryption: All data encrypted in transit and at rest
- Access Logging: Track all access to log data
- Retention Controls: Configure data retention periods
- Geographic Controls: Control data processing locations
Audit Trail
- Configuration Changes: Log all security setting changes
- Access Records: Maintain records of data access
- Token Usage: Track token usage patterns
- IP Access: Log IP address access attempts
Troubleshooting
Common Issues
- Authentication Failures: Verify token is correct and active
- IP Blocking: Check if IP is in whitelist
- Custom Headers: Ensure headers are properly configured
- Token Expiry: Confirm token hasn't been reset
Diagnostic Steps
- Verify Token: Check token matches settings
- Test Network: Confirm IP is whitelisted
- Check Headers: Validate custom header configuration
- Review Logs: Check for authentication error messages
Next Steps
- Log Visualization - View logs with proper security settings
- Alerts & Workflows - Set up security-related alerts
- Project Token Configuration - Learn more about token configuration