Viewing Detections
Scanner results
The Detections page shows all secrets found by the ByteHide Secret Scanner in your codebase.
Accessing the Detections Dashboard
- Log in to ByteHide Cloud
- Select your project
- Click on the Detections tab
 Click to expand
Click to expand
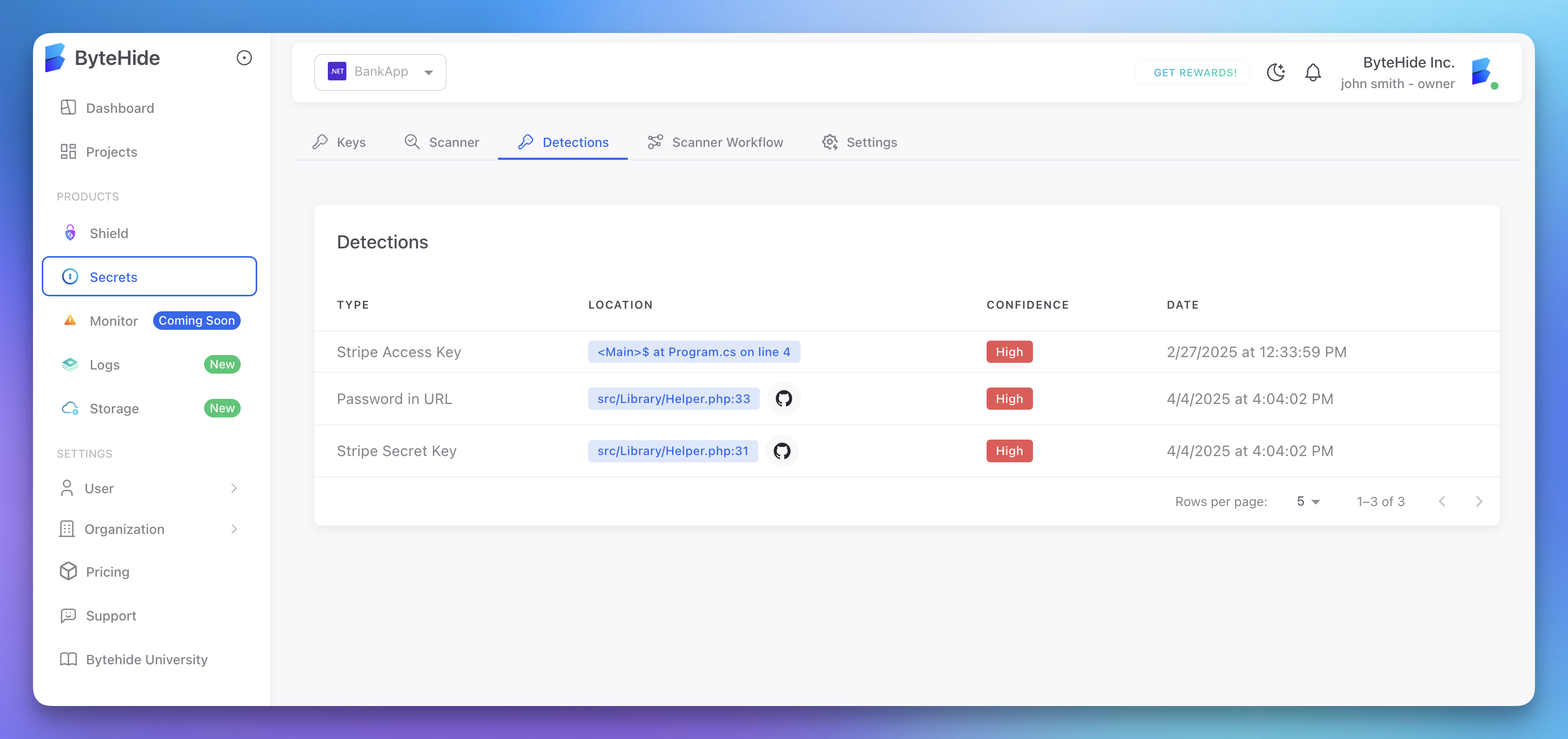
Understanding Detections
The Detections dashboard shows:
- Type: What kind of secret was detected (API key, password, etc.)
- Location: Where the secret was found (file path and line number)
- Confidence: How sure the scanner is that this is a real secret
- Date: When the secret was detected
- Repository: Which repository or application contained the secret
Viewing Detection Details
Click on a detection to see more details:
- The detected value (if DisplayCode is enabled)
- The code context where the secret was found
- Options to export or ignore the detection
 Click to expand
Click to expand
Confidence Levels
Detections are labeled with confidence levels:
- High: Very likely to be a real secret (red)
- Medium: Probably a secret (yellow)
- Low: Might be a secret (blue)
Focus on high confidence detections first, as they represent the highest security risk.
Filtering Detections
Use the filters to narrow down the results:
- Type: Filter by the type of secret
- Date Range: View detections from a specific time period
- Confidence: Filter by confidence level
- Repository/Application: View detections from specific sources
Exporting Detected Secrets
When you find a legitimate secret, you can export it to your Secrets Manager:
- Click on the detection
- Click Export to Secrets Manager
- Enter a key name
- Select the environments to export to
- Click Export
This helps you transition from hardcoded secrets to the secure Secrets Manager.
Ignoring False Positives
Sometimes the scanner might identify a value that isn't actually a secret. To ignore these:
- Click on the detection
- Click Ignore Detection
- Enter a reason for ignoring (optional)
- Click Confirm
Ignored detections can be viewed by clicking the Show Ignored filter.
Automatic Actions
The scanner can be configured to take automatic actions when secrets are detected:
- Auto-Export: Automatically export detected secrets to the Secrets Manager
- Notifications: Send alerts when secrets are detected
- Build Failure: Optionally fail builds when secrets are found
Configure these options in the Scanner Configuration.
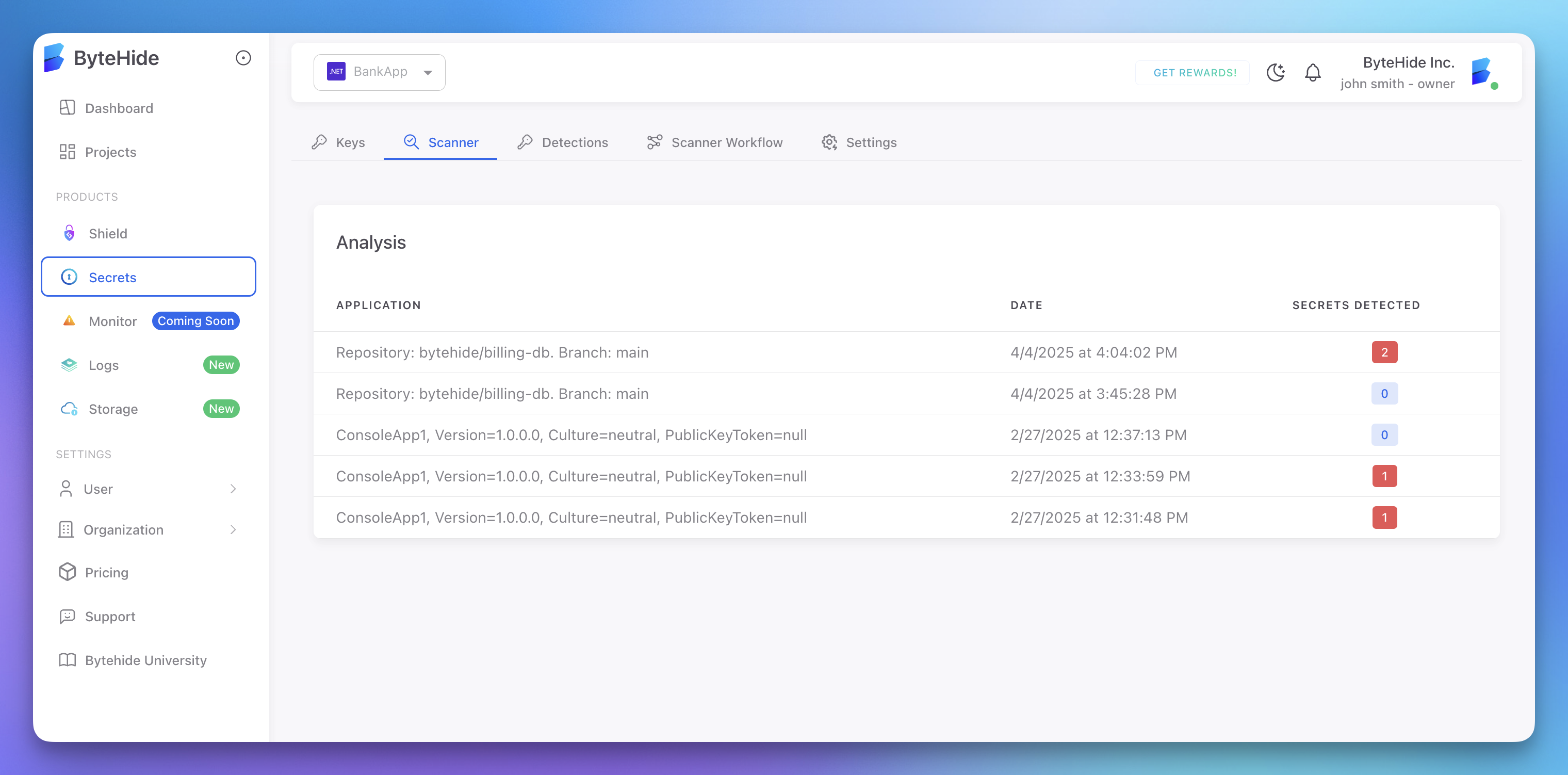
Scan History
View the history of all scans:
- Click on the Scanner tab
- Go to the Analysis sub-tab
- View all past scans with their results
 Click to expand
Click to expand
This helps you track when secrets were introduced and whether your security is improving over time.
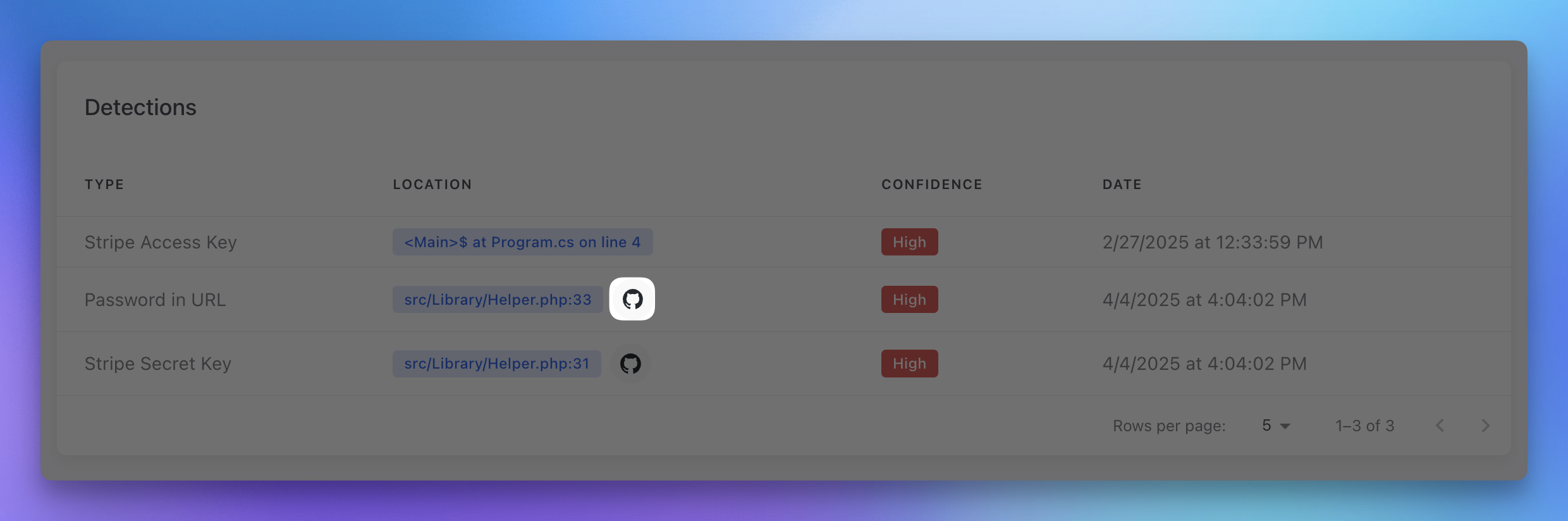
Repository Integration
For GitHub-connected repositories:
- Click on a detection
- Click the GitHub link to view the exact location in your repository
 Click to expand
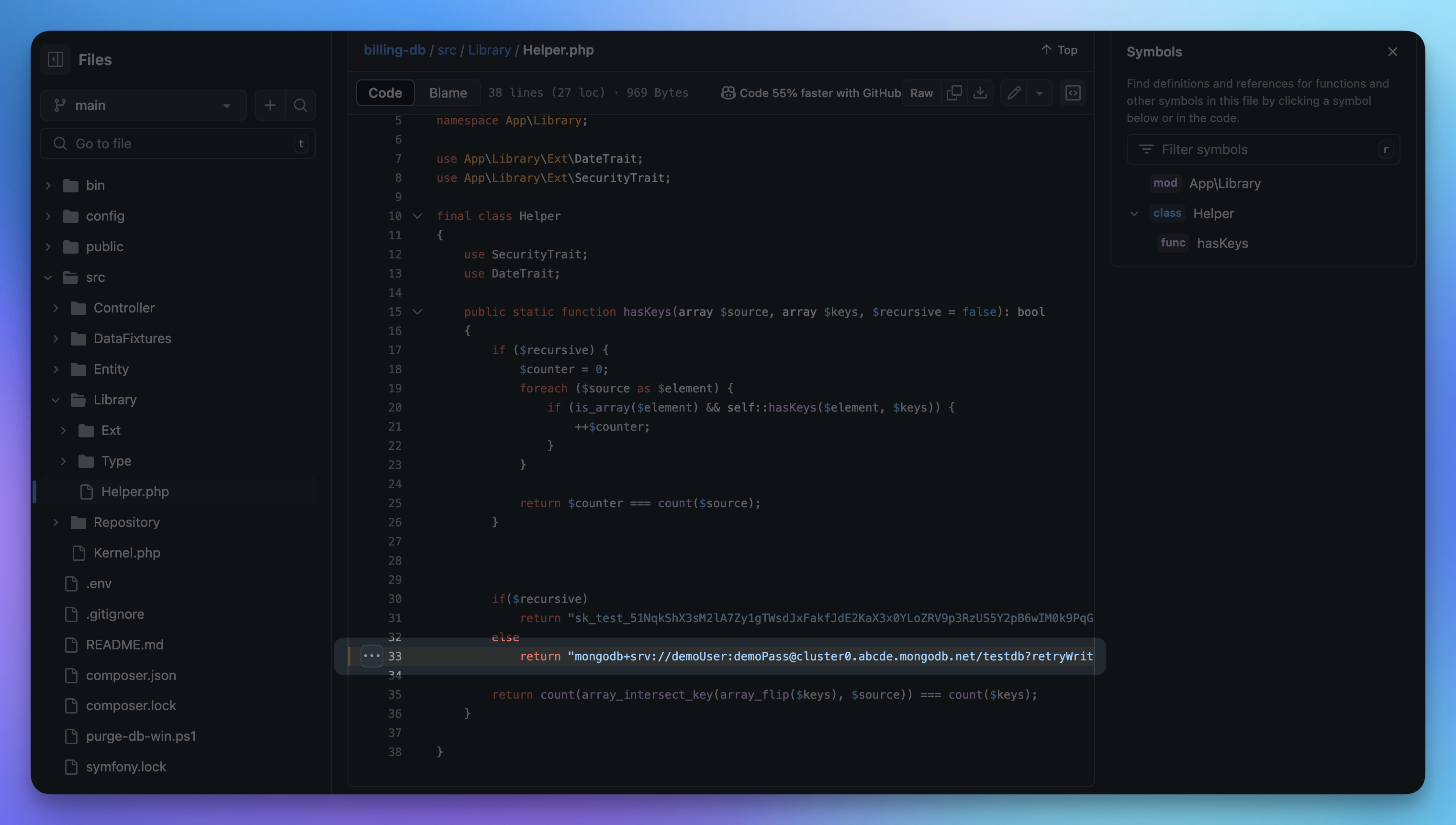
Click to expand - Fix the issue directly in your code
 Click to expand
Click to expand
Best Practices
Regular Reviews
Schedule regular reviews of your detections:
- Set a weekly or bi-weekly calendar reminder
- Review any new detections
- Export legitimate secrets to the Secrets Manager
- Ignore false positives
Remediation Workflow
When a secret is detected:
- Immediately revoke the compromised secret if possible
- Create a new secret in the Secrets Manager
- Update your application to use the Secrets Manager
- Commit the fix to remove the hardcoded secret